Today is more about reading, learning, and implementing file permissions
In Linux file structure is very important and there come the permissions to work with these files. Before we proceed with file permission let's take a look at the Linux file structure once.
File Structure:
/bin: User binaries (Common Linux command need to use in single-user mode)
/sbin: System binaries (Commands under this is for system maintenance purpose used by system admins)
/etc: Config files (etc: extended text configuration)
/dev: Device files
/proc: Process info (Contains running process info, Once the system gets rebooted then all the related files will get clear and will create new info. because it retrieves information from kernel and memory.)
/var: Variable files (It contains logs)
/tmp: Temporary files (Contains temporary files created by the system and user, Once system get reboot then all the files will get clear)
/usr: User programs (USR: Unix system resource. Contains binaries, libraries documentation files. Under it we have bin(Eg: less, awk) and sbin(Eg: cron,sshd) which contains binary files for user programs.)
/home: Home directories
/boot: Boot loader files(kernel files, grub files etc)
/lib: System libraries(Contains library files that supports the binaries that are located in /bin and /sbin)
/opt: Optional add-on apps(Contains add on installed application related files)
/mnt: Mount directory (To mount any foreign device temporarily)
/media : Removable device(To mount any removable device)
/srv: Service data (Contains server-specific service data)
Representation Of Characters In File System:
Dot(.): dot represents the current directory in the file system
Dot-Dot(. .): It represents a previous or one level above the directory
Slash(/): It represents the root of the file system. Every directory is nested under the root or you can say everything in Linux starts with (/).
Tilde(~): It represents the logged in user's home directory
File Permission:
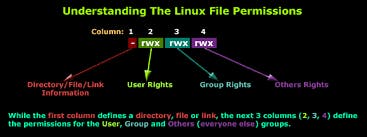
File permission is Linux determines who can access the files and directories.
How To Read Linux File Permission?
It is a set of 10 characters represented as: -rwxrwxrwx.
The first "-" will represent if it is a directory or a file. For example: If it is written as
"drwxrwxrwx", is a directory. However, if it is denoted as "-rwxrwxrwx", it is known as a file.
This string is an expression of three different sets of permissions:
rw-
r--
r--
The first set of permissions applies to the owner of the file. The second set of permissions applies to the user group that owns the file. The third set of permissions is generally referred to as "others." All Linux files belong to an owner and a group.
When permissions and users are represented by letters, that is called symbolic mode. For users, u stands for user owner, g for the group owner, and o for others. For permissions, r stands for read, w for write, and x for execute.
Every file and directory in your UNIX/Linux system has the following 3 permissions defined for all the 3 owners discussed above.
Read: This permission give you the authority to open and read a file. Read permission on a directory gives you the ability to list its content.
Write: The write permission gives you the authority to modify the contents of a file. The write permission on a directory gives you the authority to add, remove and rename files stored in the directory. Consider a scenario where you have to write permission on a file but do not have write permission on the directory where the file is stored. You will be able to modify the file contents. But you will not be able to rename, move or remove the file from the directory.
Execute: In Windows, an executable program usually has an extension “.exe” which you can easily run. In Unix/Linux, you cannot run a program unless the execute permission is set. If the execute permission is not set, you might still be able to see/modify the program code(provided read & write permissions are set), but not run it.
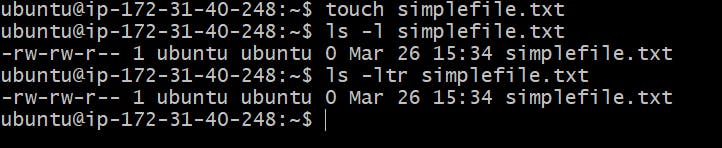
Example: Create a simple file and do ls -ltr to see the details of the files
The Octal Value Of permission is denoted as:
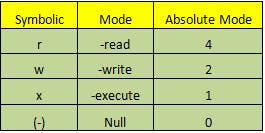
For example:
First, rwx stands for user therefore its octal value will be 7 by adding (r=4, w=2, x=1) followed by a second set of rwx by group and a third rwx set by others
The highest permission is denoted as 777.
How to modify the permissions:
chown: It is used to change the ownership permission of the file or directory
chgrp: It is used to change the group permission of a file or directory
chmod: It is used to modify the permissions of a file or directory
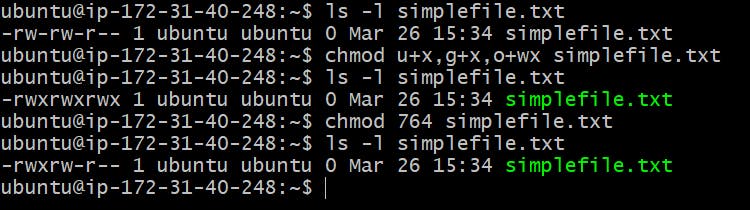
In the above example, I tried to permit the user, group, and others to execute permission to the user and group and write and execute permission to others.
In the second command, I modified the permission with octal value with r(4)+w(2)+x(1)=7 permission to the user; r(4)+w(2)=6 permission to group, and r(4) to others which makes it to 764.
What is Access Control List?
Access control list (ACL) provides an additional, more flexible permission mechanism for file systems. It is designed to assist with UNIX file permissions. ACL allows you to give permissions for any user or group to any disc resource.
Use of ACL :
Think of a scenario in which a particular user is not a member of the group created by you but still you want to give some read or write access, how can you do it without making the user a member of the group, here comes in picture Access Control Lists, ACL helps us to do this trick.
Basically, ACLs are used to make a flexible permission mechanism in Linux.
From Linux man pages, ACLs are used to define more fine-grained discretionary access rights for files and directories.
Commands to assign and remove ACL permissions are: setfacl and getfacl
List of commands for setting up ACL:
To add permissions for user:
setfacl -m u:user:rwx /path/to/fileTo add permissions for group
setfacl -m u:user:rw /path/to/fileTo allow all files or directories to inherit the ACL entries from the directories it is within
setfacl -dm "entry" path/to/dirTo remove the specific entry
surface -x u: user path/to/file (for a specific user)To remove all entries
setfacl -b path/to/file
Lab Demo:
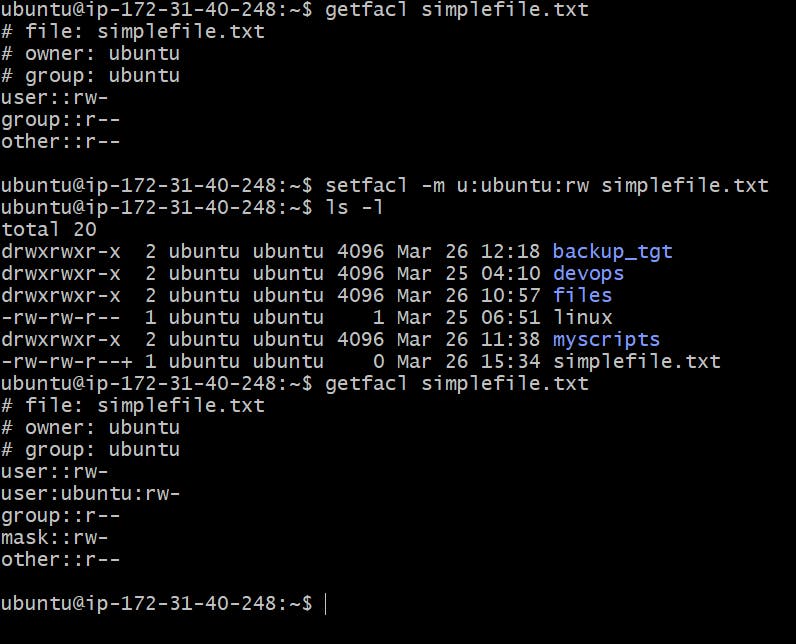
Note:
-m is used to modify the permissions
-u is used for the user
- x is used to delete permission for a single user
-b is used to delete all entries
Thank you all for reading my blog post.
